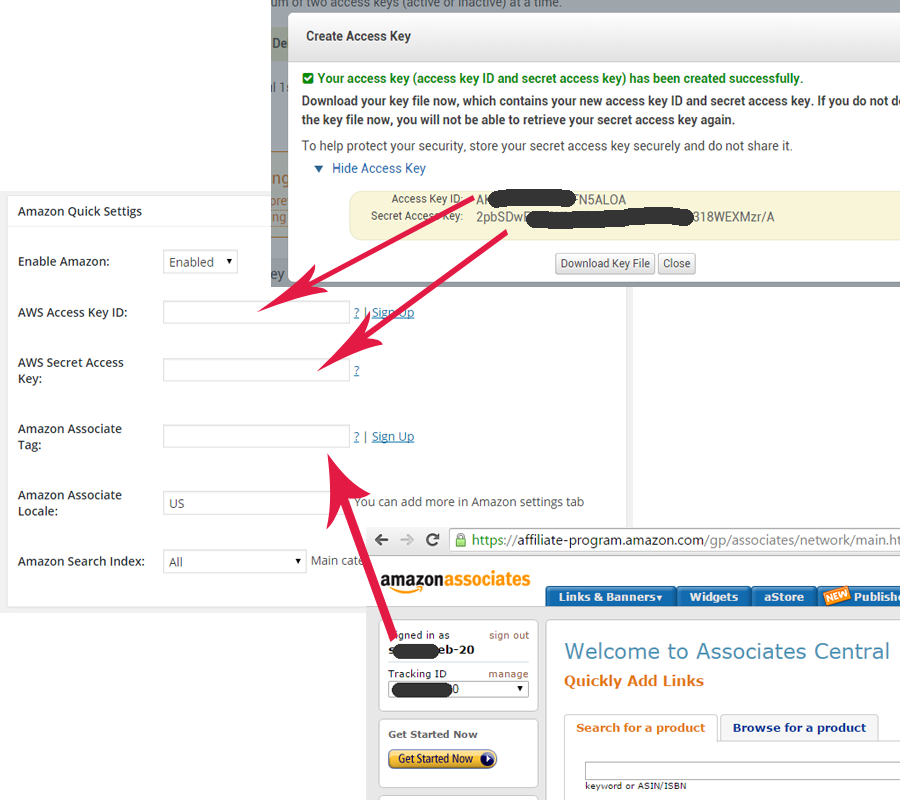
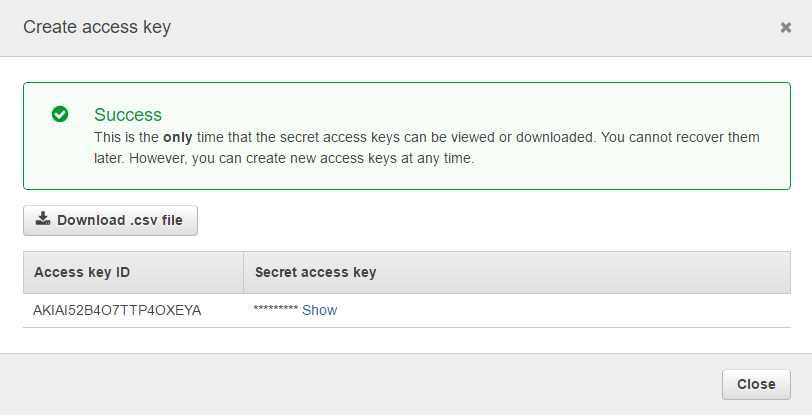
How to Create an Access Key and Secret Key in IAM The process for creating an access key is straightforward. Jump into the IAM console and find the user you want to create the access key for. Next, you’ll click the “security credentials” tab and then click the “create access key” button. To create access keys for your AWS account root user, you must use the AWS Management Console. A newly created access key has the status of active, which means that you can use the access key.
Grid 2 cd key generator. Now you can have everything for free! Get the Grid 2 Generator!
This Python example shows you how to manage the access keys of your users.
The Scenario¶
Users need their own access keys to make programmatic calls to AWS from the Amazon Web Services (AWS)SDK for Python. To fill this need, you can create, modify, view, or rotate access keys(access key IDs and secret access keys) for IAM users. By default, when you create an access key, itsstatus is Active, which means the user can use the access key for API calls.
In this example, Python code is used to manage access keys in IAM. The code uses the AWS SDK for Pythonto manage IAM access keys using these methods of the IAM client class:
- create_access_key.
- paginate(UserName='IAM_USER_NAME').
- get_access_key_last_used.
- update_access_key.
- delete_access_key.
For more information about IAM access keys, see Managing Access Keysin the IAM User Guide.
All the example code for the Amazon Web Services (AWS) SDK for Python is available here on GitHub.
On the other hand, if it’s simply a false positive, the user can allow the process to continue executing.Installation of RansomWhere? Will stop the process and present an alert to the user.If this suspected ransomware, is indeed malicious, the user can terminate the process. Once such a process is detected, RansomWhere? Ransomwhere app for mac. To Protect Your MacPatrick Wardle, a former NSA staffer who now leads research at bug hunting outfit Synack, has developed the, which aims at detecting and blocking generic ransomware on Mac OS X by regularly monitoring the user’s local filesystem for the creation of encrypted files by any process.This free tool attempts to generically prevent ransomware from taking hold of your data, by detecting untrusted processes that are encrypting your personal files.
Prerequisite Task¶

To set up and run this example, you must first configure your AWS credentials, as described in Quickstart. Jdk 8 mac os x download.
Create Access Keys for a User¶
Create a new AWS secret access key and corresponding AWS access key ID for the specified user. Thedefault status for new keys is Active.
The example below shows how to:
- Create a new AWS access key usingcreate_access_key.
Example¶
List a User's Access Keys¶
List information about the access key IDs associated with the specified IAM user. If there are none,the action returns an empty list.
Skype business cant access download mac. If the UserName field is not specified, the UserName is determined implicitly based on the AWS accesskey ID used to sign the request. Because this action works for access keys under the AWS account,you can use this action to manage root credentials even if the AWS account has no associated users.
Mac ad cleaner. The example below shows how to: Best software to record gameplay on mac.
How to download tinder on my mac computer. Why create a Tinder version for PC?No need to go through its solutions more or less convenient to use Tinder on PC.
- List a user's access keys usingpaginate(UserName='IAM_USER_NAME').
For more information about paginators see, Paginators
Example¶
Get the Access Key Last Used¶
Get information about when the specified access key was last used. The information includes thedate and time of last use, along with the AWS service and region that were specified in the last requestmade with that key.
The example below shows how to:
- Get the access key last used usingget_access_key_last_used.
Example¶
Update Access Key Status¶
Change the status of the specified access key from Active to Inactive, or vice versa. This actioncan be used to disable a user's key as part of a key rotation work flow.
The example below shows how to:
Without charge and without any risk. We’re pleased to be able to make these game cd keys available to our visitors. While we generate your cd key, you can just relax and give us a share on some social networks. We make sure you 100% safety.Title:Release date: 17 September 2013Developer: Rockstar NorthPlatform: Microsoft Windows, PlayStation 4, Xbox OneGenre: Action-adventureIf you have generated a cd key for yourself no one will be able to get that activation code again – it is like buying the game, you own GTA V game key, but you do not have to pay a great deal of cash for it.GTA V key generator is based on a algorithm, and today this tool can help you to generate your own GTA V free cd key. Steam gta 5 key generator torrent.
This is the process that worked for me. Mac os 10.10 download location. Same thing Apple said.Nothing further to contribute at this time but I will be sure to post any progress and/or solution.
.IntroductionIguana only supports OpenSSL SSH-2 private keys and certificates in PEM format, these must not be password protected. Note: Iguana will not accept SSH format defined in RFC4716, even though the format looks similar:OpenSSL: Create a public/private key file pair This section shows you how to create a public/private key file using OpenSSL.To generate a public/private key file on a Windows system:. Task How to create self-certified SSL certificate and public/private key files. Iguana accepts the older “Traditional” (or “SSLeay”) PKCS#5 format (as defined in RFC2890) or in the newer PKCS#8 format (as defined in RFC5958). Generate private and public key pair openssl.
- Change the status of an access key to Active usingupdate_access_key.
Example¶
Delete an Access Key¶
Delete the access key pair associated with the specified IAM user.
Products were delivered on time, with quality as promised. Painless, pleasant, very satisfactory window 7 home premium key product key As advertised, fast shipping, great price! Bt price for norton internet security 2012 Everything was fine. Windows 8 serial key generator 2014. I would order from them again.
Strikethrough command windows. Hidden – Alt + HTrick: You don’t need to remember all the shortcuts. If you take a close look, one letter is underlined on each effect’s label. All caps – Alt + A.
If you do not specify a user name, IAM determines the user name implicitly based on the AWS accesskey ID signing the request. Because this action works for access keys under the AWS account, you canuse this action to manage root credentials even if the AWS account has no associated users.
The example below shows how to:
Secret Access The Vatican
- Delete an access key usingdelete_access_key.